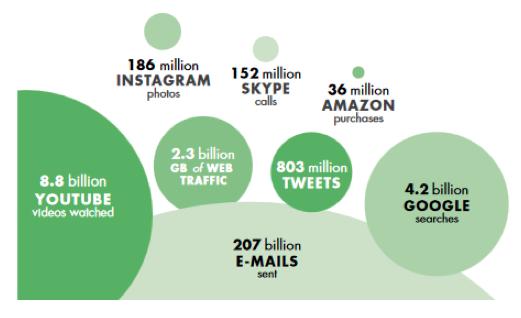
Cyber risk, long recognised as a cause for concern in the national security domain, is now also understood as a threat from the macroeconomic point of view, as an increasing share of value added is produced through ICT-enabled means. In 2012, information industries alone accounted for 6% of total value added, 4% of employment and 12% of total fixed investments in the OECD area, while ICT-related patents made up 40% of total patents filed under the Patent Cooperation Treaty (OECD 2014, 2015). In 2014, the digital sector – a narrow subsample of all ICT-enabled industries – employed 1.4 million people and accounted for 7.3% of the economy in the UK (UK Department for Culture, Media and Sport 2016). These are very conservative lower bounds for the size of the value added provided to the economy as a whole by digital technology. An alternative, suggestive description of the pervasiveness of digitalisation was proposed by the World Bank (2016) by picturing a typical day in the life of the internet (Figure 1).
Figure 1 A day on the internet, according to the World Bank
Source: World Bank, World Development Report 2016 team, http://www.internetlivestats.com/one-second (as compiled on May 29, 2015)
Not only is digitalisation spreading fast, but by its very nature it deepens the level of interconnectedness within the economy. Hence, the impact of cyber attacks goes beyond damage caused to individual victims. By the same token, a widespread perception of cyber insecurity could slow the pace of technology adoption and trade integration in knowledge-intensive sectors, hurting productivity (World Economic Forum 2014).
In order to make cyberspace safer, it is necessary to understand that cybersecurity is not just a question of good coding; it is also, if not mostly, a matter of economic incentives.
More than 15 years ago, Anderson (2001) pointed out that the incidence of automatic teller machine (ATM) fraud in different countries depended on liability rules, rather than the technical ability of fraudsters. In the US, where the banks bore the loss unless criminal intent on the part of a client could be proven, fraud was far less frequent compared to jurisdictions where the loss stayed with the cardholder.1
The sophisticated attacks known as Advanced Persistent Threats (APTs), often sponsored by nation states, are certainly an important part of the cybersecurity problem (Center for International and Strategic Studies 2016); however, significant damage is often caused by simple attacks, which could be stopped with a mixture of elementary security training, widely available defensive software, and good organisational practices. In 2013, the point-of-sale (POS) system of American retailer Target was breached, resulting in losses of about $300 million; criminals entered the system via an account stolen from a low-security provider of air-conditioning services. In 2017, hackers used a basic technique known as ‘Domain Name System (DNS) hijacking’ to redirect all online operations of a Brazilian bank to fake (‘phishing’) websites for about five hours, stealing the credentials of every client who tried to log in.
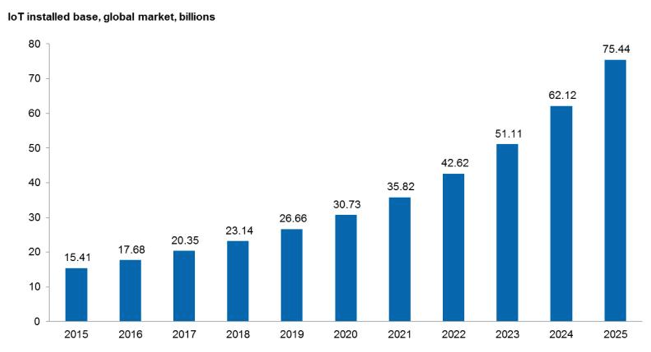
The growth of the Internet of Things (Figure 2) – the network of internet-connected, or ‘smart’, devices that perform operations in the physical world – will open a new, yet uncharted territory, and exemplifies the tradeoff between new technologies with great potential and the risk of a setback in their adoption if cybersecurity is not tackled at both a technical and economic level. Internet of Things-mediated attacks have already happened: in 2016, about 100,000 digital video recorders and web cameras were used to disrupt the operations of social platforms Twitter and Reddit, among others; in 2017, hacked vending machines took a whole university offline.
Figure 2 Projected growth of the Internet of Things
Source: IHS – Markit, as reported in Forbes
Policy solutions and policy challenges
Such incidents could be prevented by policies that neutralise the various market failures acting as a barrier to optimal private investment in cybersecurity. Beyond political will, two obstacles lie on the way of good policies, the incomplete understanding of the microeconomics of cyber security and the lack of reliable, transparent data on cyber attacks.
Anderson and Moore (2011) outline the key microeconomic determinants of cyber insecurity. First of all, the market for hardware and software is characterised by network externalities, i.e. the use value of a product increases with the number of users.2 Network externalities yield a first-mover advantage: the producer who is fastest in attracting a sufficiently large user base sets the standard, which in turn brings in more users. This mechanism underlies the oligopolistic structure of hardware and software markets, and yielded the ‘release now, patch later’ model of development; as security is still not perceived as essential by customers, it is overlooked in the race for minimum time to market, leading to a lot of built-in weakness.
Second, cyber vulnerabilities have negative externalities: the cost of a breach may not fall entirely on the immediate victim. Many computer systems store valuable information about entities other than the system’s owners. For example, the attacks against health insurer Anthem and e-mail provider Yahoo! damaged all customers whose sensitive medical records or personal communications were unduly accessed. Also, hackers often use indirect attack techniques – rather than going for their ultimate target directly, they first take control of any unprotected machine they can find, then launch their offensive from those. Some networks of hijacked computers, known as botnets, comprise millions of units.
Despite all this, awareness of cyber risk is still generally low, and even if no externalities of any kind were present, many users of IT systems would not invest enough in security because they do not understand the risks. And even if they did, a principal-agent problem would still exist between them and vendors of defensive systems, leading to suboptimal protection. Hardware and software producers have so far eschewed liability for insecure products by arguing that attaching a financial burden to inevitable errors in computer code would kill the incentive to innovate; as recently pointed out by The Economist (2017), public perception and the stance of legislators could change drastically the moment a hacked smart car ran someone over.
Several options to eliminate negative externalities have been proposed, most aimed at balancing the need to internalise the costs of breaches with the idea that an ordinary citizen whose Internet of Things washing machine is hijacked to attack an oil company should not be forced to compensate it. One example is selective liability, whereby specialised agents such as internet service providers (ISPs) would bear some of the cost of attacks that transit on the networks they manage.3
Most OECD countries are starting to develop cybersecurity legislation that provides partial solutions to market failures, for example by mandating that custodians of personal data disclose breaches to the owners of the information that was illegally accessed, or by imposing security requirements for critical infrastructure whose failure could damage the general public. In tech-intensive, security-conscious sectors, stringent national legal obligations are complemented by international regulatory standards and best practices.
The financial sector, which is very attractive to hackers of all stripes (Maurer et al. 2017), provides a good illustration of the interplay between these levels. In advanced economies, legislation subjects financial institutions to closer scrutiny, stricter compliance requirements, and tougher liability rules compared to most other businesses. For example, starting in 2018 payment service providers in the EU will have to comply with the new Payment Services Directive (PSD2), which mandates very high standards of cybersecurity for all digital payments.4
Central banks and other financial regulators can also impose obligations on supervised entities, such as disclosure of significant cyber incidents, at the same time cooperating to develop security standards that, while non-binding, are recognised internationally and constitute a reference for the implementation of national laws. The Bank for International Settlements and the International Organization of Securities Commissions fostered a transnational drive for enhanced security of the financial system; this resulted in a Guidance on Cyber Resilience for Financial Market Infrastructures (BIS and IOSCO 2016) that is not limited to technical aspects, but also tackles governance, the role of the human factor, and the importance of information sharing.
All of these efforts minimise, but do not eliminate, the risk of facing new crisis scenarios. For example, a large financial institution could be perfectly solvent, yet inoperable on account of a cyber attack. Securing any single sector, while useful, is still not enough. Economy-wide policies are needed – no point of cyberspace can be safe if the surrounding environment is not. Contrary to most existing legislation, policies should apply to all types of attacks, not only those that involve personal data, and to all economic agents, not only critical infrastructure or providers of certain services.
The data gap: A key policy challenge
Good policy design is hampered by a serious lack of data. How vulnerable are ordinary businesses? How often are they attacked? What is the cost of security? Very little is known. The statistics most often quoted in the media are provided by companies that specialise in cyber defence, carrying an obvious conflict of interest, and the underlying micro-level information is not public. Very few attempts have been made to produce data of appropriate quality and transparency.
One example is the UK Government’s Survey of Cyber Security Breaches, first conducted in 2016; the most recent results were published in April 2017 (UK Department for Culture, Media and Sport 2017). According to the survey, 46% of UK firms were hit by at least one cyber attack in the 12 months prior to the interview, with the incidence of breaches increasing with size, peaking at 68% among large businesses (Figure 3). While the mean damage caused by attacks was relatively modest (£19,600 among large firms), the distribution was asymmetrical; the most disruptive breach recorded in the dataset implied £500,000 of recovery costs alone.
Figure 3 Incidence of cyber attacks on UK firms
Source: UK Government.
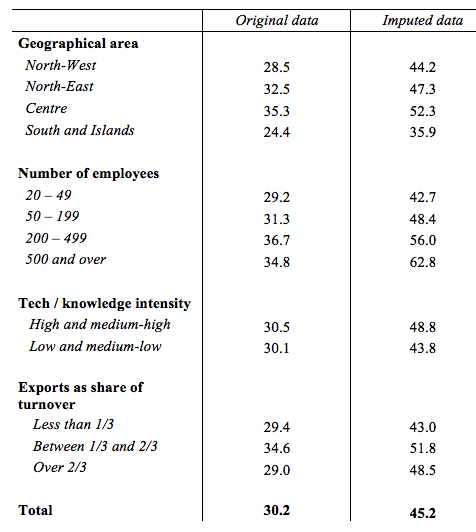
A similar, if less detailed, exercise was conducted by the Bank of Italy (Biancotti 2017), leveraging the long-standing surveys of Italian manufacturing and non-financial service firms.[5] Even though fewer than 2% of businesses declared that they do not deploy any cybersecurity measures, about one third suffered at least some damage from a cyber attack between September 2015 and September 2016 (Table 1). An imputation model was developed to account for the unwillingness to report or the inability to detect attacks for some respondents; the share of firms attacked during the observed period climbed to 45.2, with large, high-tech and internationally exposed businesses faring worse than average.
Table 1 Share of Italian manufacturing and non-financial service firms hit by at least one cyber attack
These data should be a wake-up call for governments and public institutions. More information of this kind, ideally based on internationally harmonised definitions and made available to researchers at no cost, are needed with some urgency in order to develop appropriate responses at the technical, economic and legal level.
Authors’ note: The views expressed in this note should not be attributed to the Bank of Italy.
References
Anderson, R (2001), ‘Why Information Security is Hard – an Economic Perspective’, Proceedings of the 17th Annual Computer Security Applications Conference.
Anderson, R and T Moore (2011), ‘Internet Security’, in Peitz, M. and J. Waldfogel (eds.), The Oxford Handbook of the Digital Economy, Oxford University Press.
Biancotti, C (2017), ‘Cyber Attacks: Preliminary Evidence from the Bank of Italy’s Business Surveys’, Occasional Papers no. 373, Bank of Italy.
Bank for International Settlements and Board of the International Organization of Securities Commissions (2016), ‘Guidance on Cyber Resilience for Financial Market Infrastructures’.
Center for Strategic and International Studies (2016), ‘Significant Cyber Incidents since 2006’.
Maurer, T, A Levite and G Perkovitch (2017), ‘Toward a Global Norm Against Manipulating the Integrity of Financial Data’, Carnegie Endowment for International Peace White Paper.
Messerschmidt, J (2013), ‘Hackback: Permitting Retaliatory Hacking by Non-State Actors as Proportionate Countermeasures to Transboundary Cyberharm’, Columbia Journal of Transnational Law, 52(1).
OECD (2014), ‘Measuring the Digital Economy. A New Perspective’.
OECD (2015), ‘Digital Economy Outlook’.
Raymond, M, G Nojeim and A Brill (2015), ‘Private Sector Hack-backs and the Law of Unintended Consequences’, Center for Democracy & Technology.
The Economist (2017), ‘How to Manage the Computer-Security Threat’.
UK Department for Culture, Media and Sport (2017), ‘Cyber Security Breaches Survey: Main Report’.
UK Department for Culture, Media and Sport (2016), ‘Digital Sector Economic Estimates – Statistical Release’.
World Bank (2016), World Development Report 2016: Digital Dividends.
World Economic Forum (2014), ‘Risk and Responsibility in a Hyperconnected World’.
Endnotes
[1] Eventually, in the face of increasing crime, liability was attributed to banks almost everywhere, triggering adequate investments in ATM security.
[2] This is particularly evident in the case of operating systems – a widely installed operating system is more appealing for application developers, and an operating system which supports many applications is more appealing for users. Another example is given by messaging platforms, whose value is zero if they do not connect anyone.
[3] A lively debate also exists on the right of self-defense as applied to the cyber realm, with ‘hack-backs’ sometimes presented as one of the best responses to the many attacks originating from non-cooperative jurisdictions (Messerschmidt 2013), and sometimes heavily criticised as a source of further insecurity (Raymond et al. 2015).
[4] In the PSD2 framework, security will be guaranteed through a holistic approach that involves four domains: users, payment services providers, communication infrastructures, and authorities.
[5] These are: the Survey of Industrial and Service Firms (https://www.bancaditalia.it/pubblicazioni/indagine-imprese/index.html), focusing on structural variables, and the Business Outlook Survey of Industrial and Service Firms (https://www.bancaditalia.it/pubblicazioni/sondaggio-imprese/index.html), focusing on short-term dynamics. Both are carried out every year.